VPN Safety or virtual private network broadens the assets of the network to encompass the more unrestricted networks, for example the World-wide-web, making use of a wide region network (WAN) link or a point-to point connection, to connect the websites, applying encryption and dedicated connections, but, all the time, giving the impression to the user of applying a private link. Given that traveling more rapidly than the speed of light is tantamount to breaking the time barrier, this daunting prospect has brought on some physicists to try to come up with increasingly elaborate ways to clarify away Aspect’s findings. This contrasts with created countries where more than 30% have access at a price of 1%.
It is also unclear whether or not current SAR devices could effortlessly help such a mode of operation. Performing a header error correction function for a single or a lot more of the asynchronous transfer mode cells received. Transmission convergence sublayer 18 recognizes a beginning and finish of an asynchronous transfer mode cell and checks its payload for website traffic or null data.
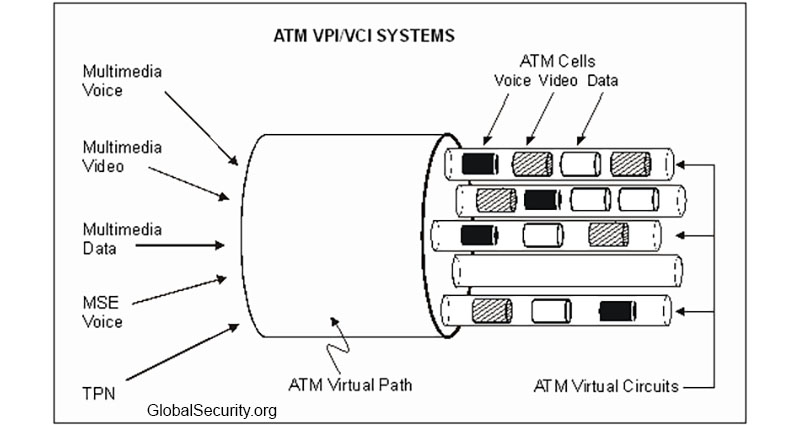
Discarding one particular or more of the asynchronous transfer mode cells that do not carry a payload. As far as targeted traffic is concerned asynchronous transfer mode specifically makes use of virtual network for driving site visitors within various places.
If an asynchronous transfer mode cell has null info in its payload, then transmission convergence sublayer discards the null cell. The following figure, Traditional LAN: Connectionless Information Transmittal of a Packet, shows an example of a standard LAN. Sustainable Cell Rate (SCR) – a calculation of the connection’s average cell transfer price.
The AAL5 CRC uses the similar CRC-32 algorithm applied in 802.x-based networks such as Ethernet and Token Ring. This is accurate for the whole breadth of the network if bandwidth or speed exceeds the limits established by the contract, any device, which includes the ATM adapter, can simply drop the information.