This question could be answered just or it may be answered in very a bit of detail. The uncomplicated answer is that information is sent across networks digitally. The expanded answer is the fact that data is sent across networks in digital form, using several protocols and routing solutions. This short article will touch lightly on the digital format that I utilized and introduce you to the network protocols which can be applied.
Digital Implies Binary
When you speak around the (analog) telephone or in a particular person with someone, that you are sending an analog signal to that particular person. Your voice is continuously modulated to kind the letters, words, and inflections of everyday speech. When that conversation enters the digital arena, the information and facts, your conversation, is converted into digital signals. Digital signals imply the electrical existing is either on or off. This is also known as …
View More How Data Is Transferred Over a Network

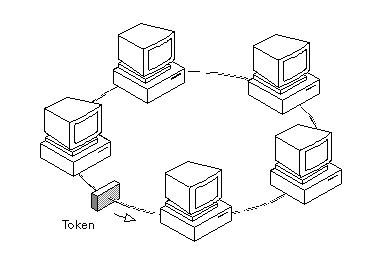 A wide range of unique neighborhood location network technologies were created in the early 1970s, of which one, the Cambridge Ring had demonstrated the possible of a token passing ring topology , and many teams worldwide began functioning on their personal implementations. If any of these phases fail, the Token Ring station will not insert into the ring and the Token Ring driver could report an error. For far more details about ring speed specifications, refer to the hardware installation and upkeep manual for your technique.
A wide range of unique neighborhood location network technologies were created in the early 1970s, of which one, the Cambridge Ring had demonstrated the possible of a token passing ring topology , and many teams worldwide began functioning on their personal implementations. If any of these phases fail, the Token Ring station will not insert into the ring and the Token Ring driver could report an error. For far more details about ring speed specifications, refer to the hardware installation and upkeep manual for your technique. A Token Ring network is a neighborhood location network (LAN) in which all computer systems are connected in a ring or star topology and a bit- or token-passing scheme is utilised in order to prevent the collision of data in between two computer systems that want to send messages at the same time. If you ran Token Ring at 16Mbps, you could have a packet size up to 18,200 bytes long. New switching technologies and more rapidly versions of Token-Ring are in the operates to speed network throughput (see the facts on Higher Speed Token-Ring earlier in this section).
A Token Ring network is a neighborhood location network (LAN) in which all computer systems are connected in a ring or star topology and a bit- or token-passing scheme is utilised in order to prevent the collision of data in between two computer systems that want to send messages at the same time. If you ran Token Ring at 16Mbps, you could have a packet size up to 18,200 bytes long. New switching technologies and more rapidly versions of Token-Ring are in the operates to speed network throughput (see the facts on Higher Speed Token-Ring earlier in this section).
 One of the major technologies battles of the 80’s and 90’s was Token Ring vs. Ethernet. Having said that, the actual ring on which the token is circulated is a logical ring inside of the MAU. Use the show operating-config privileged exec command to decide which speed is specified on the router. Token Ring vendors tried to increase the speed of the technologies to 100Mbps to overcome the Ethernet positive aspects, but by the time they did at the turn of the century, it was also late.
One of the major technologies battles of the 80’s and 90’s was Token Ring vs. Ethernet. Having said that, the actual ring on which the token is circulated is a logical ring inside of the MAU. Use the show operating-config privileged exec command to decide which speed is specified on the router. Token Ring vendors tried to increase the speed of the technologies to 100Mbps to overcome the Ethernet positive aspects, but by the time they did at the turn of the century, it was also late.